Discover how a bimodal integration strategy can address the major data management challenges facing your organization today.
Get the Report →Use the CData JDBC Driver for Amazon Athena in MicroStrategy Web
Connect to Amazon Athena data in MicroStrategy Web using the CData JDBC Driver for Amazon Athena.
MicroStrategy is an analytics and mobility platform that enables data-driven innovation. When you pair MicroStrategy with the CData JDBC Driver for Amazon Athena, you gain database-like access to live Amazon Athena data from MicroStrategy, expanding your reporting and analytics capabilities. In this article, we walk through adding Amazon Athena as an external data source in MicroStrategy Web and creating a simple visualization of Amazon Athena data.
The CData JDBC driver offers unmatched performance for interacting with live Amazon Athena data in MicroStrategy due to optimized data processing built into the driver. When you issue complex SQL queries from MicroStrategy to Amazon Athena, the driver pushes supported SQL operations, like filters and aggregations, directly to Amazon Athena and utilizes the embedded SQL engine to process unsupported operations (often SQL functions and JOIN operations) client-side. With built-in dynamic metadata querying, you can visualize and analyze Amazon Athena data using native MicroStrategy data types.
Connect to and Visualize Amazon Athena Data using MicroStrategy Web
You can connect to Amazon Athena in MicroStrategy Web by adding a data source based on the CData JDBC Driver for Amazon Athena.* Before you begin, you will need install the JDBC Driver for Amazon Athena on the machine hosting the MicroStrategy Intelligence Server that your instance of MicroStrategy Web is connected to. Once you have created a data source you can build dynamic visualizations of Amazon Athena data in MicroStrategy Web.
- Open MicroStrategy Web and select your project.
- Click Add External Data, select Databases, and use Select Tables as the Import Option.
![Adding External Data]()
- In the Import from Tables wizard, click to add a new Data Source.
- Select Generic in the Database menu and select Generic DBMS in the Version menu.
- Click the link to show the connection string and opt to edit the connection string. In the Driver menu, select MicroStrategy Cassandra ODBC Driver (MicroStrategy requires a certified driver to interface through JDBC, the actual driver will not be used).
- Set the connection string to the following:
JDBC;MSTR_JDBC_JAR_FOLDER=PATH\TO\JAR\;DRIVER=cdata.jdbc.amazonathena.AmazonAthenaDriver;URL={jdbc:amazonathena:AccessKey='a123';SecretKey='s123';Region='IRELAND';Database='sampledb';S3StagingDirectory='s3://bucket/staging/';};![Configure the data source.]()
Authenticating to Amazon Athena
To authorize Amazon Athena requests, provide the credentials for an administrator account or for an IAM user with custom permissions: Set AccessKey to the access key Id. Set SecretKey to the secret access key.
Note: Though you can connect as the AWS account administrator, it is recommended to use IAM user credentials to access AWS services.
Obtaining the Access Key
To obtain the credentials for an IAM user, follow the steps below:
- Sign into the IAM console.
- In the navigation pane, select Users.
- To create or manage the access keys for a user, select the user and then select the Security Credentials tab.
To obtain the credentials for your AWS root account, follow the steps below:
- Sign into the AWS Management console with the credentials for your root account.
- Select your account name or number and select My Security Credentials in the menu that is displayed.
- Click Continue to Security Credentials and expand the Access Keys section to manage or create root account access keys.
Authenticating from an EC2 Instance
If you are using the CData Data Provider for Amazon Athena 2018 from an EC2 Instance and have an IAM Role assigned to the instance, you can use the IAM Role to authenticate. To do so, set UseEC2Roles to true and leave AccessKey and SecretKey empty. The CData Data Provider for Amazon Athena 2018 will automatically obtain your IAM Role credentials and authenticate with them.
Authenticating as an AWS Role
In many situations it may be preferable to use an IAM role for authentication instead of the direct security credentials of an AWS root user. An AWS role may be used instead by specifying the RoleARN. This will cause the CData Data Provider for Amazon Athena 2018 to attempt to retrieve credentials for the specified role. If you are connecting to AWS (instead of already being connected such as on an EC2 instance), you must additionally specify the AccessKey and SecretKey of an IAM user to assume the role for. Roles may not be used when specifying the AccessKey and SecretKey of an AWS root user.
Authenticating with MFA
For users and roles that require Multi-factor Authentication, specify the MFASerialNumber and MFAToken connection properties. This will cause the CData Data Provider for Amazon Athena 2018 to submit the MFA credentials in a request to retrieve temporary authentication credentials. Note that the duration of the temporary credentials may be controlled via the TemporaryTokenDuration (default 3600 seconds).
Connecting to Amazon Athena
In addition to the AccessKey and SecretKey properties, specify Database, S3StagingDirectory and Region. Set Region to the region where your Amazon Athena data is hosted. Set S3StagingDirectory to a folder in S3 where you would like to store the results of queries.
If Database is not set in the connection, the data provider connects to the default database set in Amazon Athena.
Built-in Connection String Designer
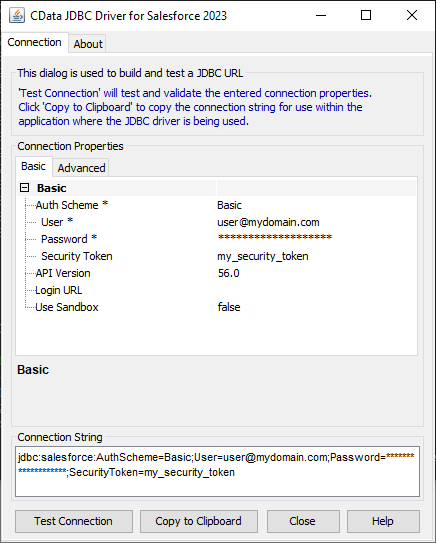
For assistance in constructing the JDBC URL, use the connection string designer built into the Amazon Athena JDBC Driver. Either double-click the JAR file or execute the jar file from the command-line.
java -jar cdata.jdbc.amazonathena.jarFill in the connection properties and copy the connection string to the clipboard.
![Using the built-in connection string designer to generate a JDBC URL (Salesforce is shown.)]()
When you configure the JDBC URL, you may also want to set the Max Rows connection property. This will limit the number of rows returned, which is especially helpful for improving performance when designing reports and visualizations.
- Right-click on the new data source, and choose Edit catalog options.
![Edit the catalog options.]()
- Edit the SQL Statement to SELECT * FROM SYS_SCHEMAS to read the metadata from the JDBC Driver.
![Configuring the Catalog Options.]()
- Select the new data source to view the available tables. You may need to manually click the search icon in the Available Tables section to see the tables.
- Drag tables into the pane to import them.
![Select tables to import.]() Note: Since we create a live connection, we can import whole tables and utilize the filtering and aggregation features native to the MicroStrategy products to customize our datasets.
Note: Since we create a live connection, we can import whole tables and utilize the filtering and aggregation features native to the MicroStrategy products to customize our datasets. - Click Finish, choose to the option to connect live, save the query, and choose the option to create a new dossier. Live connections are possible and effective, thanks to high-performance data processing native to CData JDBC drivers.
![Save the query and create a new dossier.]()
- Choose a visualization, choose fields to display and apply any filters to create a new visualization of Amazon Athena data. Data types are discovered automatically through dynamic metadata discovery. Where possible, the complex queries generated by the filters and aggregations will be pushed down to Amazon Athena, while any unsupported operations (which can include SQL functions and JOIN operations) will be managed client-side by the CData SQL engine embedded in the driver.
![Visualize Amazon Athena data.]()
- Once you have finished configuring the dossier, click File -> Save.
Using the CData JDBC Driver for Amazon Athena in MicroStrategy Web, you can easily create robust visualizations and reports on Amazon Athena data. Read our other articles on connecting to Amazon Athena in MicroStrategy and connecting to Amazon Athena in MicroStrategy Desktop for more examples.
Note: Connecting using a JDBC Driver requires a 3- or 4-Tier Architecture.










 Note: Since we create a live connection, we can import whole tables and utilize the filtering and aggregation features native to the MicroStrategy products to customize our datasets.
Note: Since we create a live connection, we can import whole tables and utilize the filtering and aggregation features native to the MicroStrategy products to customize our datasets.

