ノーコードでクラウド上のデータとの連携を実現。
詳細はこちら →
CData


こんにちは!ドライバー周りのヘルプドキュメントを担当している古川です。
SQL Gateway を使って、MySQL リモーティングサービスを作成し、Amazon Athena のMySQL Federated Table を構築できます。CData ODBC Driver for AmazonAthena のMySQL インターフェースのdeamon になります。サービス起動後、MySQL のFEDERATED ストレージエンジンを使ってサーバーおよびテーブルを作成します。Amazon Athena データ をMySQL テーブルのように使いましょう。
If you have not already done so, provide values for the required connection properties in the data source name (DSN). You can use the built-in Microsoft ODBC Data Source Administrator to configure the DSN. This is also the last step of the driver installation. See the "Getting Started" chapter in the help documentation for a guide to using the Microsoft ODBC Data Source Administrator to create and configure a DSN.
Amazon Athena リクエストの認証には、アカウントの管理のクレデンシャルか、IAM ユーザーのカスタムPermission を設定します。 AccessKey にAccess Key Id、SecretKey にはSecret Access Key を設定します。
AWS アカウントアドミニストレータとしてアクセスできる場合でも、AWS サービスへの接続にはIAM ユーザークレデンシャルを使用することが推奨されます。
IAM ユーザーのクレデンシャル取得は以下のとおり:
AWS ルートアカウントのクレデンシャル取得は以下のとおり:
EC2 インスタンスからCData 製品を使用していて、そのインスタンスにIAM ロールが割り当てられている場合は、認証にIAM ロールを使用できます。 これを行うには、UseEC2Roles をtrue に設定しAccessKey とSecretKey を空のままにします。 CData 製品は自動的にIAM ロールの認証情報を取得し、それらを使って認証します。
多くの場合、認証にはAWS ルートユーザーのダイレクトなセキュリティ認証情報ではなく、IAM ロールを使用することをお勧めします。 代わりにRoleARN を指定してAWS ロールを使用できます。これにより、CData 製品は指定されたロールの資格情報を取得しようと試みます。 (すでにEC2 インスタンスなどで接続されているのではなく)AWS に接続している場合は、役割を担うIAM ユーザーのAccessKeyと SecretKey を追加で指定する必要があります。AWS ルートユーザーのAccessKey およびSecretKey を指定する場合、 ロールは使用できません。
多要素認証を必要とするユーザーおよびロールには、MFASerialNumber およびMFAToken 接続プロパティを指定してください。 これにより、CData 製品は一時的な認証資格情報を取得するために、リクエストでMFA 認証情報を送信します。一時的な認証情報の有効期間 (デフォルトは3600秒)は、TemporaryTokenDuration プロパティを介して制御できます。
AccessKey とSecretKey プロパティに加え、Database、S3StagingDirectory、Region を設定します。Region をAmazon Athena データがホストされているリージョンに設定します。S3StagingDirectory をクエリの結果を格納したいS3内のフォルダに設定します。
接続にDatabase が設定されていない場合は、CData 製品はAmazon Athena に設定されているデフォルトデータベースに接続します。
See the SQL Gateway Overview to set up connectivity to Amazon Athena データ as a virtual MySQL database. You will configure a MySQL remoting service that listens for MySQL requests from clients. The service can be configured in the SQL Gateway UI.
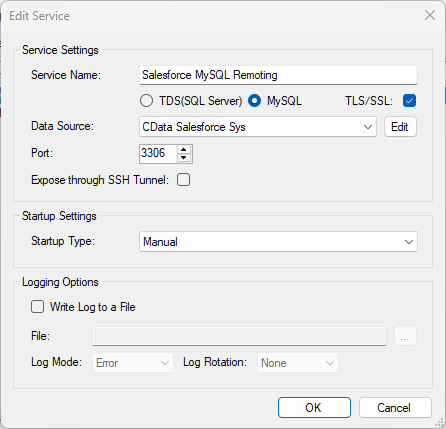
After you have configured and started the service, create a FEDERATED server to simplify the process of creating FEDERATED tables:
The following statement will create a FEDERATED server based on the ODBC Driver for AmazonAthena. Note that the username and password of the FEDERATED server must match a user account you defined on the Users tab of the SQL Gateway.
CREATE SERVER fedAmazonAthena FOREIGN DATA WRAPPER mysql OPTIONS (USER 'sql_gateway_user', PASSWORD 'sql_gateway_passwd', HOST 'sql_gateway_host', PORT ####, DATABASE 'CData AmazonAthena Sys');
To create a FEDERATED table using our newly created server, use the CONNECTION keyword and pass the name of the FEDERATED server and the remote table (Customers). Refer to the following template for the statement to create a FEDERATED table:
CREATE TABLE fed_customers ( ..., name TYPE(LEN), totaldue TYPE(LEN), ..., ) ENGINE=FEDERATED DEFAULT CHARSET=latin1 CONNECTION='fedAmazonAthena/customers';
NOTE: The table schema for the FEDERATED table must match the remote table schema exactly. You can always connect directly to the MySQL remoting service using any MySQL client and run a SHOW CREATE TABLE query to get the table schema.
You can now execute queries to the Amazon Athena FEDERATED tables from any tool that can connect to MySQL, which is particularly useful if you need to JOIN data from a local table with data from Amazon Athena. Refer to the following example:
SELECT fed_customers.name, local_table.custom_field FROM local_table JOIN fed_customers ON local_table.foreign_name = fed_customers.name;