Connecting Mastra with Amazon Athena Data via CData Connect AI MCP Server
Mastra is designed for developers and enterprise teams building intelligent, composable AI agents. Its modular framework and declarative architecture make it simple to orchestrate agents, integrate LLMs, and automate data-driven workflows. But when agents need to work with data beyond their local memory or predefined APIs, many implementations rely on custom middleware or scheduled syncs to copy data from external systems into local stores. This approach adds complexity, increases maintenance overhead, introduces latency, and limits the real-time potential of your agents.
CData Connect AI bridges this gap with live, direct connectivity to more than 300 enterprise applications, databases, ERPs, and analytics platforms. Through CData's remote Model Context Protocol (MCP) Server, Mastra agents can securely query, read, and act on real-time data without replication. The result is grounded responses, faster reasoning, and automated decision-making across systems all with stronger governance and fewer moving parts.
This article outlines the steps required to configure CData Connect AI MCP connectivity, register the MCP server in Mastra Studio, and build an agent that queries live Amazon Athena data in real time.
About Amazon Athena Data Integration
CData provides the easiest way to access and integrate live data from Amazon Athena. Customers use CData connectivity to:
- Authenticate securely using a variety of methods, including IAM credentials, access keys, and Instance Profiles, catering to diverse security needs and simplifying the authentication process.
- Streamline their setup and quickly resolve issue with detailed error messaging.
- Enhance performance and minimize strain on client resources with server-side query execution.
Users frequently integrate Athena with analytics tools like Tableau, Power BI, and Excel for in-depth analytics from their preferred tools.
To learn more about unique Amazon Athena use cases with CData, check out our blog post: https://www.cdata.com/blog/amazon-athena-use-cases.
Getting Started
Prerequisites
Before starting, make sure you have:
- A CData Connect AI account
- Node.js 18+ and npm installed
- A working Mastra project (created via npm create mastra@latest)
- Access to Amazon Athena
Credentials checklist
Ensure you have these credentials ready for the connection:
- USERNAME: Your CData email login
- PAT: Connect AI, go to Settings and click on Access Tokens (copy once)
- MCP_BASE_URL: https://mcp.cloud.cdata.com/mcp
Step 1: Configure Amazon Athena connectivity for Mastra
Connectivity to Amazon Athena from Mastra is made possible through CData Connect AI Remote MCP. To interact with Amazon Athena data from Mastra, we start by creating and configuring a Amazon Athena connection in CData Connect AI.
- Log into Connect AI, click Sources, and then click Add Connection
- Select "Amazon Athena" from the Add Connection panel
-
Enter the necessary authentication properties to connect to Amazon Athena.
Authenticating to Amazon Athena
To authorize Amazon Athena requests, provide the credentials for an administrator account or for an IAM user with custom permissions: Set AccessKey to the access key Id. Set SecretKey to the secret access key.
Note: Though you can connect as the AWS account administrator, it is recommended to use IAM user credentials to access AWS services.
Obtaining the Access Key
To obtain the credentials for an IAM user, follow the steps below:
- Sign into the IAM console.
- In the navigation pane, select Users.
- To create or manage the access keys for a user, select the user and then select the Security Credentials tab.
To obtain the credentials for your AWS root account, follow the steps below:
- Sign into the AWS Management console with the credentials for your root account.
- Select your account name or number and select My Security Credentials in the menu that is displayed.
- Click Continue to Security Credentials and expand the Access Keys section to manage or create root account access keys.
Authenticating from an EC2 Instance
If you are using the CData Data Provider for Amazon Athena 2018 from an EC2 Instance and have an IAM Role assigned to the instance, you can use the IAM Role to authenticate. To do so, set UseEC2Roles to true and leave AccessKey and SecretKey empty. The CData Data Provider for Amazon Athena 2018 will automatically obtain your IAM Role credentials and authenticate with them.
Authenticating as an AWS Role
In many situations it may be preferable to use an IAM role for authentication instead of the direct security credentials of an AWS root user. An AWS role may be used instead by specifying the RoleARN. This will cause the CData Data Provider for Amazon Athena 2018 to attempt to retrieve credentials for the specified role. If you are connecting to AWS (instead of already being connected such as on an EC2 instance), you must additionally specify the AccessKey and SecretKey of an IAM user to assume the role for. Roles may not be used when specifying the AccessKey and SecretKey of an AWS root user.
Authenticating with MFA
For users and roles that require Multi-factor Authentication, specify the MFASerialNumber and MFAToken connection properties. This will cause the CData Data Provider for Amazon Athena 2018 to submit the MFA credentials in a request to retrieve temporary authentication credentials. Note that the duration of the temporary credentials may be controlled via the TemporaryTokenDuration (default 3600 seconds).
Connecting to Amazon Athena
In addition to the AccessKey and SecretKey properties, specify Database, S3StagingDirectory and Region. Set Region to the region where your Amazon Athena data is hosted. Set S3StagingDirectory to a folder in S3 where you would like to store the results of queries.
If Database is not set in the connection, the data provider connects to the default database set in Amazon Athena.
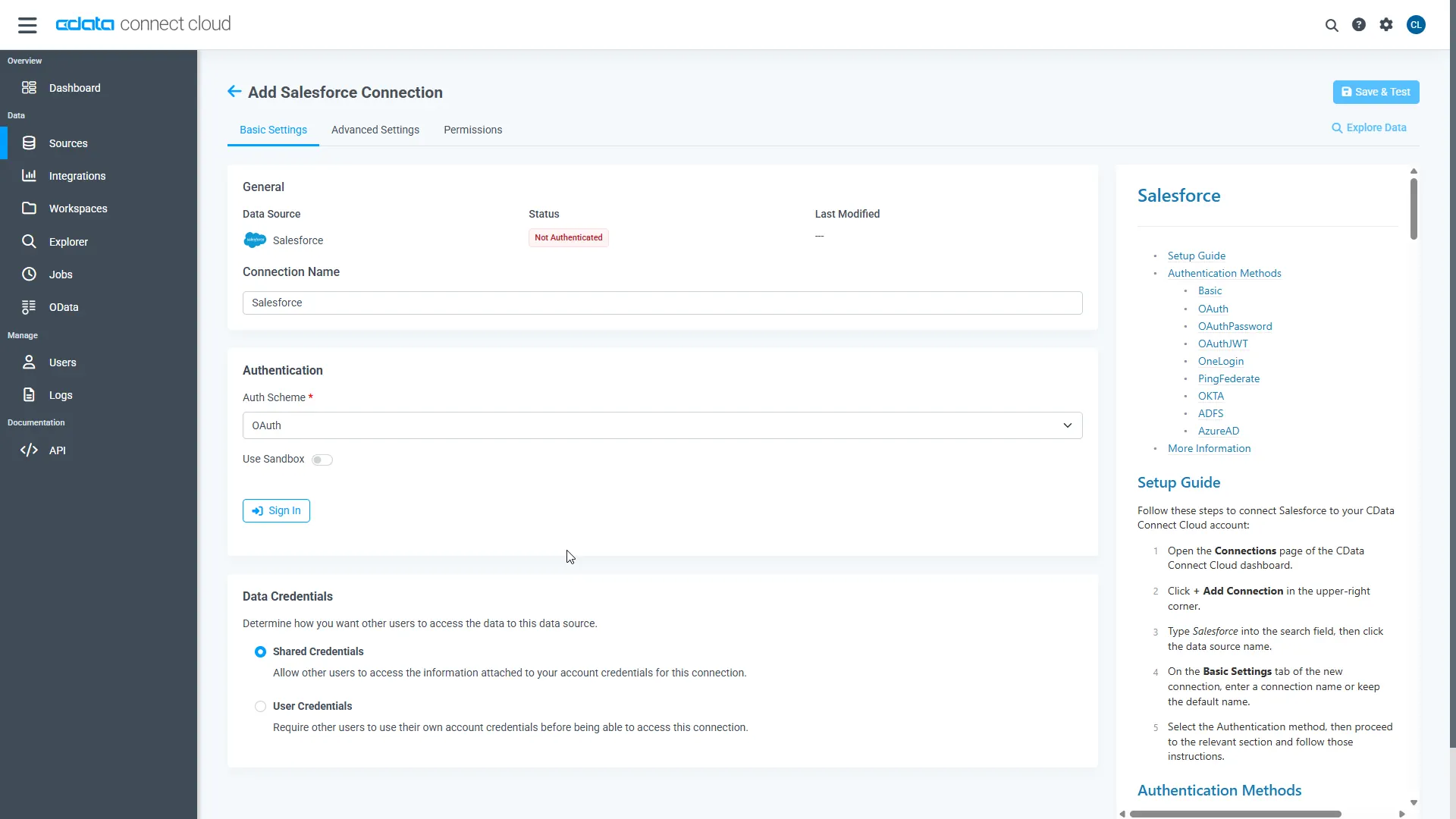
- Click Save & Test
-
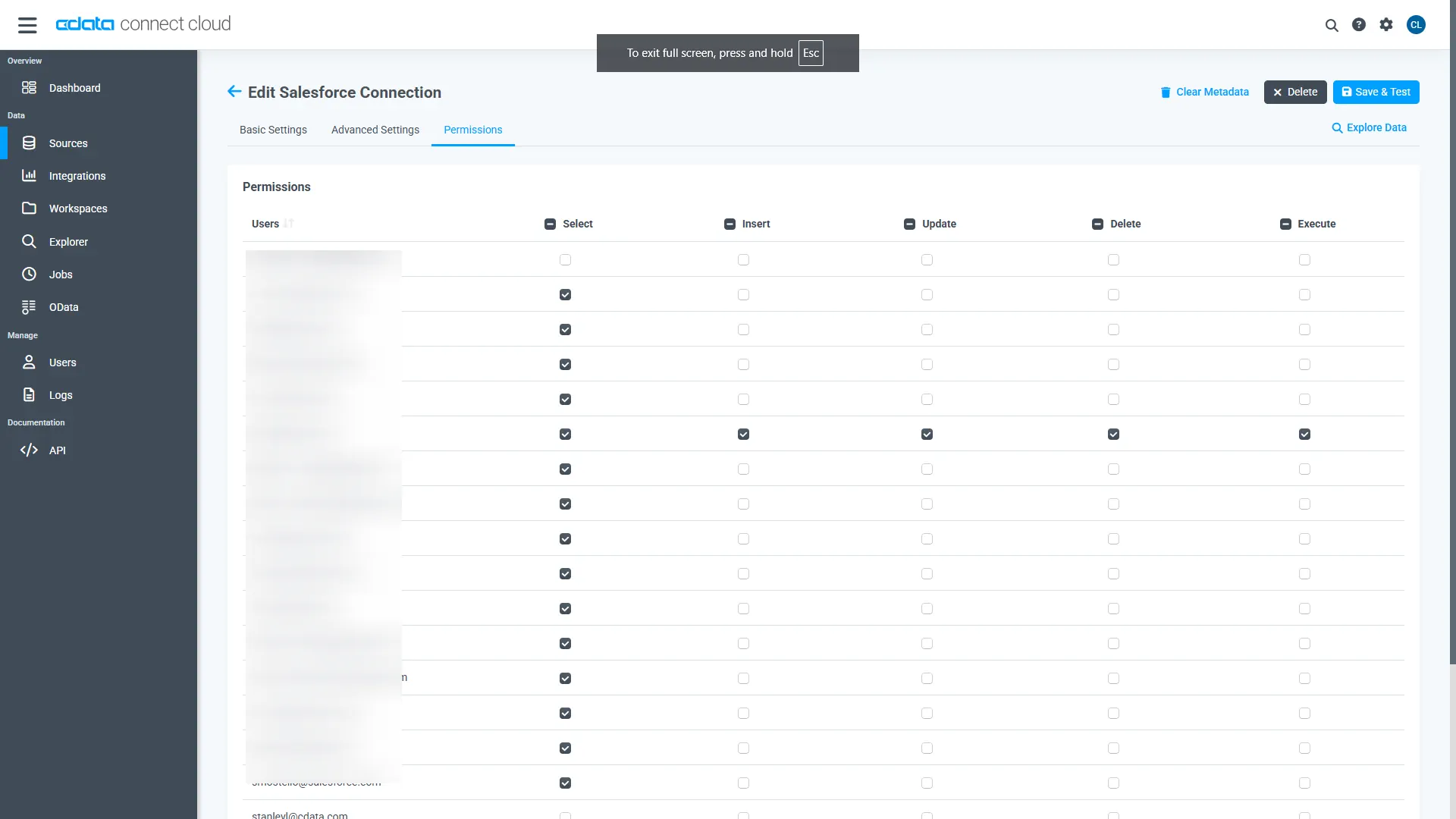
Navigate to the Permissions tab in the Add Amazon Athena Connection page and update the User-based permissions.

Add a Personal Access Token
A Personal Access Token (PAT) is used to authenticate the connection to Connect AI from Mastra. It is best practice to create a separate PAT for each service to maintain granularity of access.
- Click on the Gear icon () at the top right of the Connect AI app to open the settings page.
- On the Settings page, go to the Access Tokens section and click Create PAT.
-
Give the PAT a name and click Create.
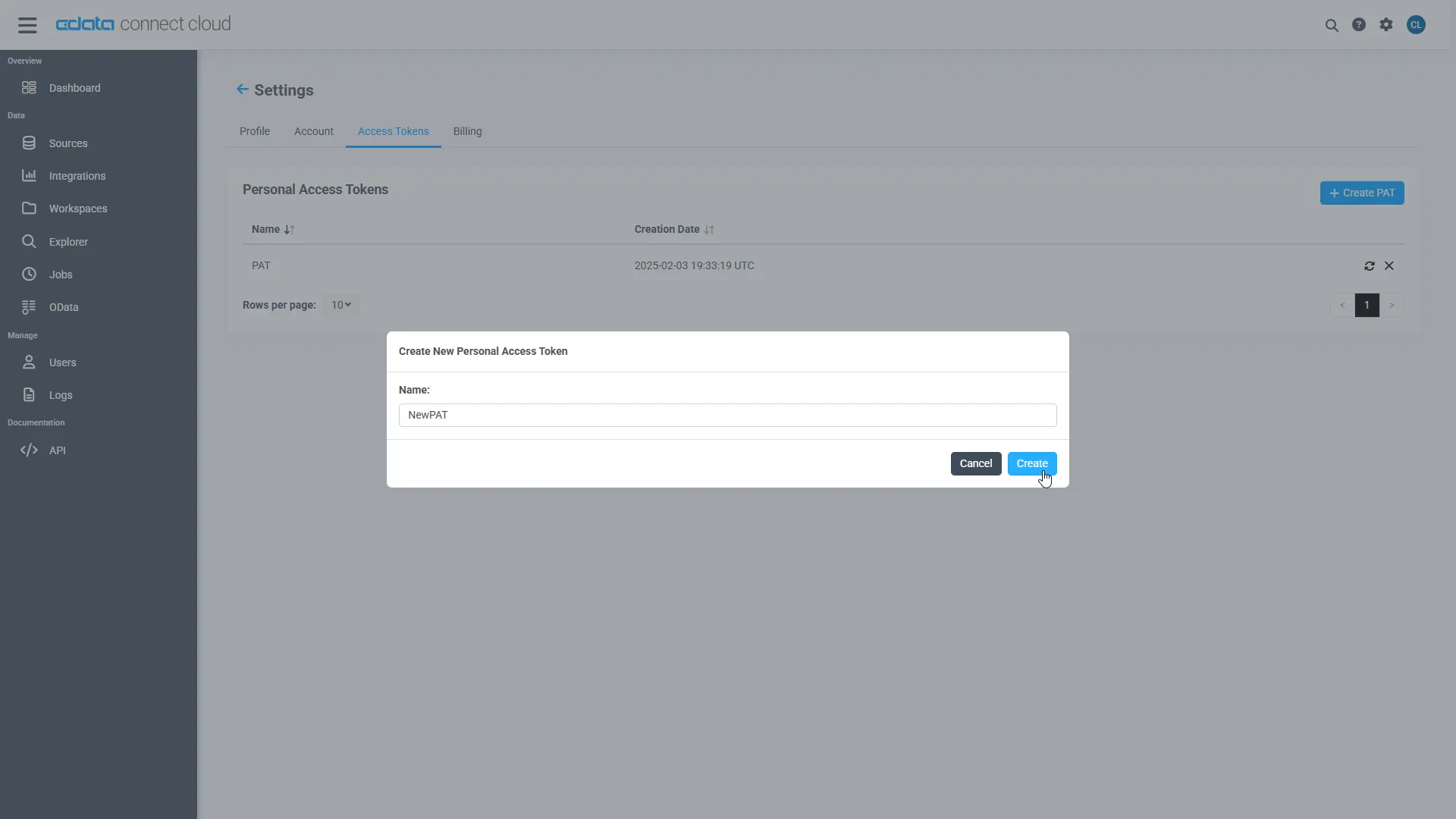
- The personal access token is only visible at creation, so be sure to copy it and store it securely for future use.
With the connection configured and a PAT generated, we are ready to connect to Amazon Athena data from Mastra.
Step 2: Set up the Mastra project
- Open a terminal and navigate to your desired folder
- Create a new project:
npm create mastra@latest
- Open the folder in VS Code
- Install the required Mastra dependencies:
npm install @mastra/core @mastra/libsql @mastra/memory
- Then install the MCP integration package separately:
npm install @mastra/mcp

Step 3: Configure environment variables
Create a .env file at the project root with the following keys:
OPENAI_API_KEY=sk-... [email protected] CDATA_CONNECT_AI_PASSWORD=your_PAT
Restart your dev server after saving changes:
npm run dev
Step 4: Add the CData Connect AI agent
Create a file src/mastra/agents/connect-ai-agent.ts with the following code:
import { Agent } from "@mastra/core/agent";
import { Memory } from "@mastra/memory";
import { LibSQLStore } from "@mastra/libsql";
import { MCPClient } from "@mastra/mcp";
const mcpClient = new MCPClient({
servers: {
cdataConnectAI: {
url: new URL("https://connect.cdata.com/mcp/"),
requestInit: {
headers: {
Authorization: `Basic ${Buffer.from(
`${process.env.CDATA_CONNECT_AI_USER}:${process.env.CDATA_CONNECT_AI_PASSWORD}`
).toString("base64")}`,
},
},
},
},
});
export const connectAIAgent = new Agent({
name: "Connect AI Agent",
instructions: "You are a data exploration and analysis assistant with access to CData Connect AI.",
model: "openai/gpt-4o-mini",
tools: await mcpClient.getTools(),
memory: new Memory({
storage: new LibSQLStore({ url: "file:../mastra.db" }),
}),
});
Step 5: Update index.ts to register the agent
Replace the contents of src/mastra/index.ts with:
import { Mastra } from "@mastra/core/mastra";
import { PinoLogger } from "@mastra/loggers";
import { LibSQLStore } from "@mastra/libsql";
import { connectAIAgent } from "./agents/connect-ai-agent.js";
export const mastra = new Mastra({
agents: { connectAIAgent },
storage: new LibSQLStore({ url: "file:../mastra.db" }),
logger: new PinoLogger({ name: "Mastra", level: "info" }),
observability: { default: { enabled: true } },
});
Step 6: Run and verify the connection
Start your Mastra server:
npm run dev

Step 7: Run a live query in Mastra Studio
In Mastra Studio, open the chat interface and enter one of the following sample prompts:
List available catalogs from my connected data sources.

Build real-time, data-aware agents with Mastra and CData
Mastra and CData Connect AI together enable powerful AI-driven workflows where agents have live access to enterprise data and act intelligently without sync pipelines or manual integration logic.
Start your free trial today to see how CData can empower Mastra with live, secure access to 300+ external systems.






