Connecting Mastra with SingleStore Data via CData Connect AI MCP Server
Mastra is designed for developers and enterprise teams building intelligent, composable AI agents. Its modular framework and declarative architecture make it simple to orchestrate agents, integrate LLMs, and automate data-driven workflows. But when agents need to work with data beyond their local memory or predefined APIs, many implementations rely on custom middleware or scheduled syncs to copy data from external systems into local stores. This approach adds complexity, increases maintenance overhead, introduces latency, and limits the real-time potential of your agents.
CData Connect AI bridges this gap with live, direct connectivity to more than 300 enterprise applications, databases, ERPs, and analytics platforms. Through CData's remote Model Context Protocol (MCP) Server, Mastra agents can securely query, read, and act on real-time data without replication. The result is grounded responses, faster reasoning, and automated decision-making across systems all with stronger governance and fewer moving parts.
This article outlines the steps required to configure CData Connect AI MCP connectivity, register the MCP server in Mastra Studio, and build an agent that queries live SingleStore data in real time.
Prerequisites
Before starting, make sure you have:
- A CData Connect AI account
- Node.js 18+ and npm installed
- A working Mastra project (created via npm create mastra@latest)
- Access to SingleStore
Credentials checklist
Ensure you have these credentials ready for the connection:
- USERNAME: Your CData email login
- PAT: Connect AI, go to Settings and click on Access Tokens (copy once)
- MCP_BASE_URL: https://mcp.cloud.cdata.com/mcp
Step 1: Configure SingleStore connectivity for Mastra
Connectivity to SingleStore from Mastra is made possible through CData Connect AI Remote MCP. To interact with SingleStore data from Mastra, we start by creating and configuring a SingleStore connection in CData Connect AI.
- Log into Connect AI, click Sources, and then click Add Connection
- Select "SingleStore" from the Add Connection panel
-
Enter the necessary authentication properties to connect to SingleStore.
The following connection properties are required in order to connect to data.
- Server: The host name or IP of the server hosting the SingleStore database.
- Port: The port of the server hosting the SingleStore database.
- Database (Optional): The default database to connect to when connecting to the SingleStore Server. If this is not set, tables from all databases will be returned.
Connect Using Standard Authentication
To authenticate using standard authentication, set the following:
- User: The user which will be used to authenticate with the SingleStore server.
- Password: The password which will be used to authenticate with the SingleStore server.
Connect Using Integrated Security
As an alternative to providing the standard username and password, you can set IntegratedSecurity to True to authenticate trusted users to the server via Windows Authentication.
Connect Using SSL Authentication
You can leverage SSL authentication to connect to SingleStore data via a secure session. Configure the following connection properties to connect to data:
- SSLClientCert: Set this to the name of the certificate store for the client certificate. Used in the case of 2-way SSL, where truststore and keystore are kept on both the client and server machines.
- SSLClientCertPassword: If a client certificate store is password-protected, set this value to the store's password.
- SSLClientCertSubject: The subject of the TLS/SSL client certificate. Used to locate the certificate in the store.
- SSLClientCertType: The certificate type of the client store.
- SSLServerCert: The certificate to be accepted from the server.
Connect Using SSH Authentication
Using SSH, you can securely login to a remote machine. To access SingleStore data via SSH, configure the following connection properties:
- SSHClientCert: Set this to the name of the certificate store for the client certificate.
- SSHClientCertPassword: If a client certificate store is password-protected, set this value to the store's password.
- SSHClientCertSubject: The subject of the TLS/SSL client certificate. Used to locate the certificate in the store.
- SSHClientCertType: The certificate type of the client store.
- SSHPassword: The password that you use to authenticate with the SSH server.
- SSHPort: The port used for SSH operations.
- SSHServer: The SSH authentication server you are trying to authenticate against.
- SSHServerFingerPrint: The SSH Server fingerprint used for verification of the host you are connecting to.
- SSHUser: Set this to the username that you use to authenticate with the SSH server.
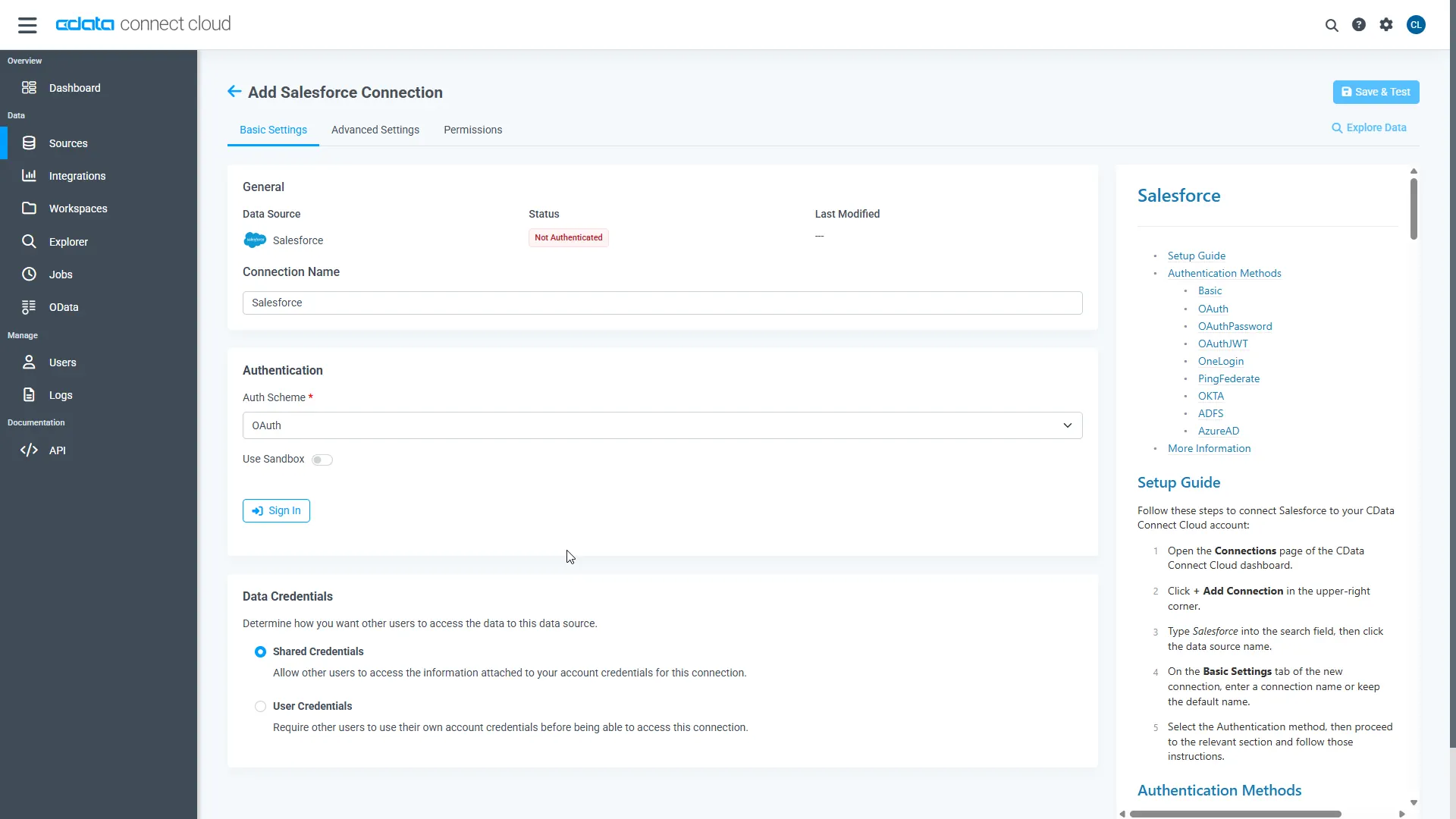
- Click Save & Test
-
Navigate to the Permissions tab in the Add SingleStore Connection page and update the User-based permissions.
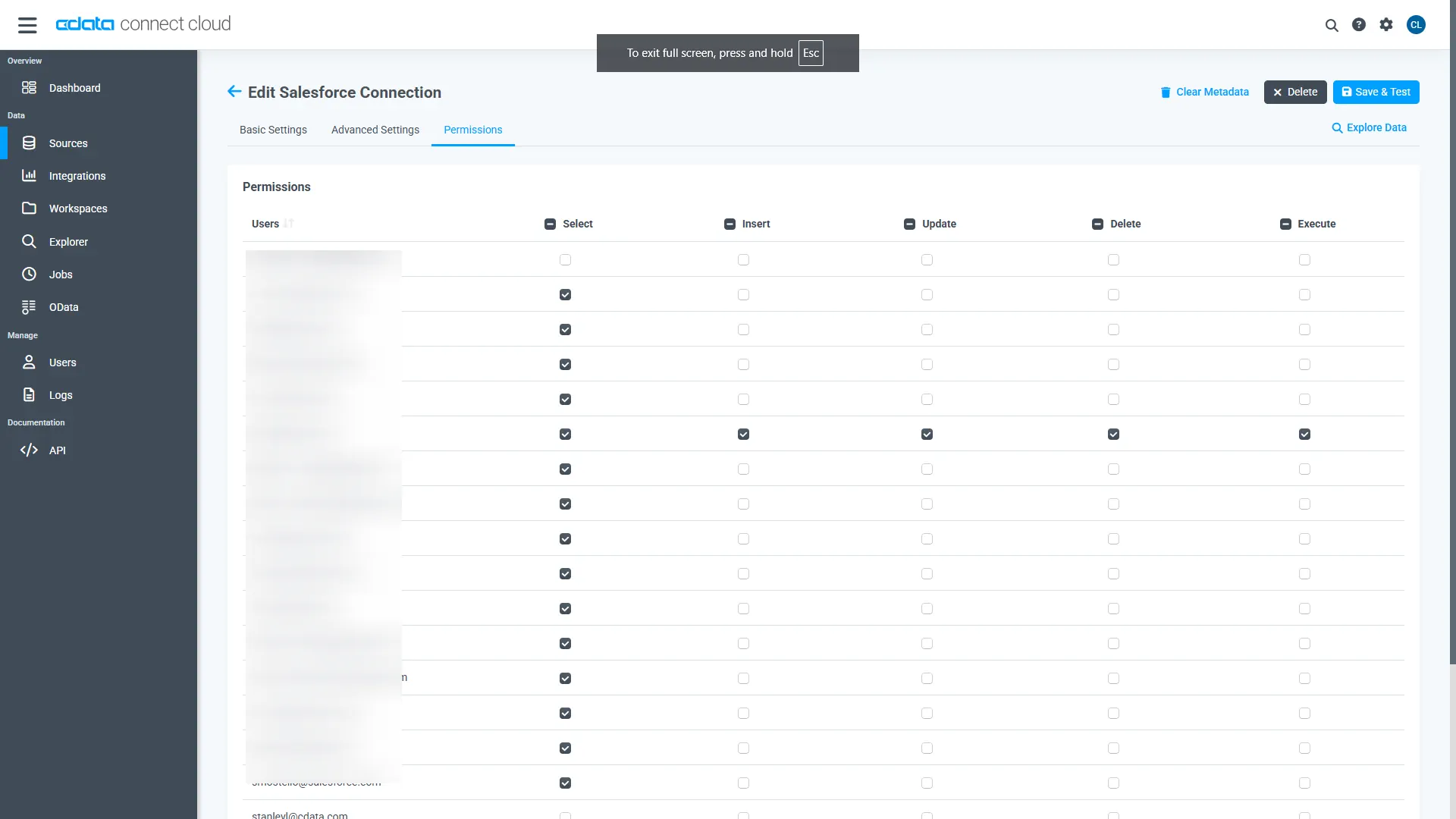

Add a Personal Access Token
A Personal Access Token (PAT) is used to authenticate the connection to Connect AI from Mastra. It is best practice to create a separate PAT for each service to maintain granularity of access.
- Click on the Gear icon () at the top right of the Connect AI app to open the settings page.
- On the Settings page, go to the Access Tokens section and click Create PAT.
-
Give the PAT a name and click Create.
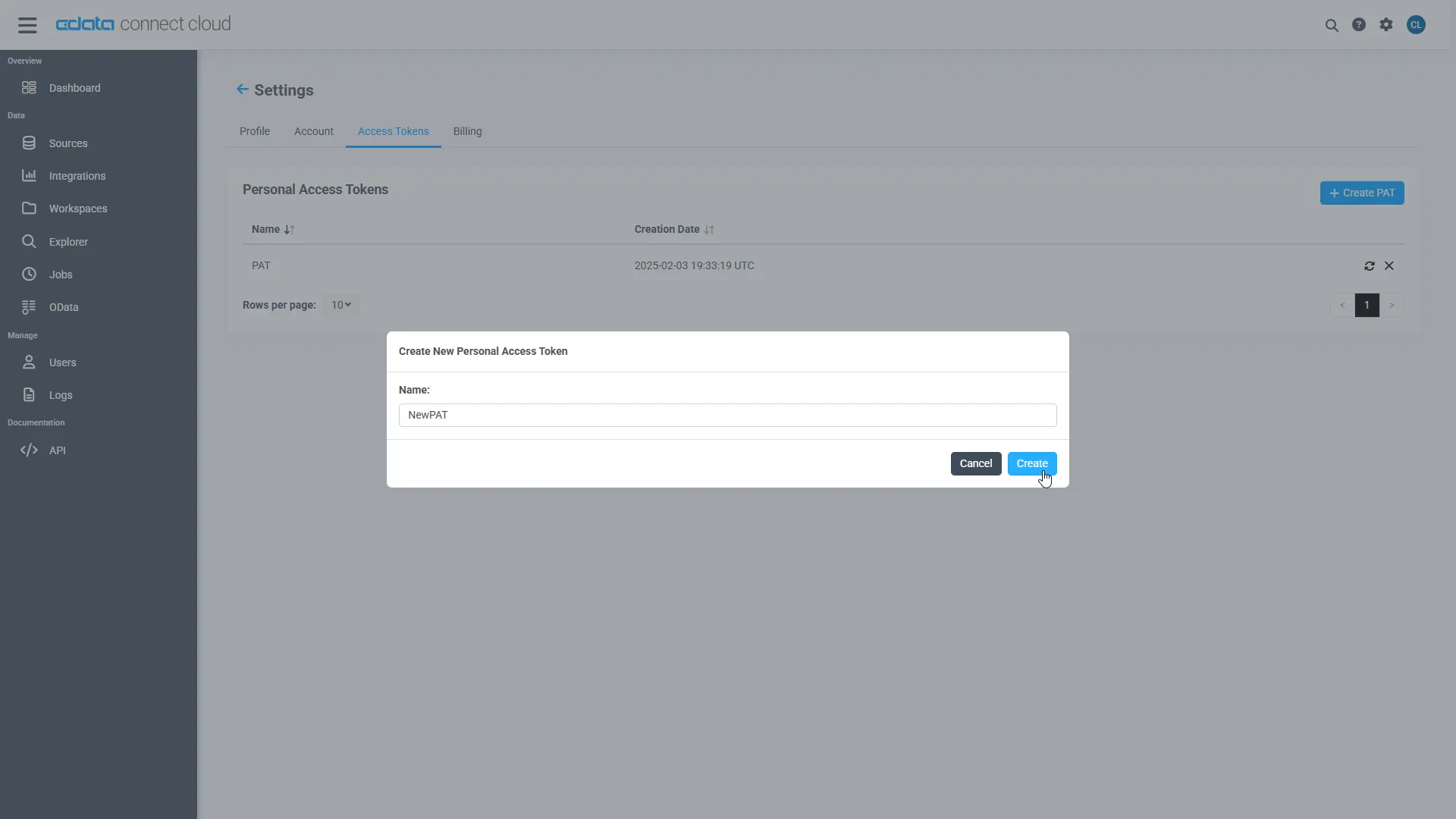
- The personal access token is only visible at creation, so be sure to copy it and store it securely for future use.
With the connection configured and a PAT generated, we are ready to connect to SingleStore data from Mastra.
Step 2: Set up the Mastra project
- Open a terminal and navigate to your desired folder
- Create a new project:
npm create mastra@latest
- Open the folder in VS Code
- Install the required Mastra dependencies:
npm install @mastra/core @mastra/libsql @mastra/memory
- Then install the MCP integration package separately:
npm install @mastra/mcp

Step 3: Configure environment variables
Create a .env file at the project root with the following keys:
OPENAI_API_KEY=sk-... [email protected] CDATA_CONNECT_AI_PASSWORD=your_PAT
Restart your dev server after saving changes:
npm run dev
Step 4: Add the CData Connect AI agent
Create a file src/mastra/agents/connect-ai-agent.ts with the following code:
import { Agent } from "@mastra/core/agent";
import { Memory } from "@mastra/memory";
import { LibSQLStore } from "@mastra/libsql";
import { MCPClient } from "@mastra/mcp";
const mcpClient = new MCPClient({
servers: {
cdataConnectAI: {
url: new URL("https://connect.cdata.com/mcp/"),
requestInit: {
headers: {
Authorization: `Basic ${Buffer.from(
`${process.env.CDATA_CONNECT_AI_USER}:${process.env.CDATA_CONNECT_AI_PASSWORD}`
).toString("base64")}`,
},
},
},
},
});
export const connectAIAgent = new Agent({
name: "Connect AI Agent",
instructions: "You are a data exploration and analysis assistant with access to CData Connect AI.",
model: "openai/gpt-4o-mini",
tools: await mcpClient.getTools(),
memory: new Memory({
storage: new LibSQLStore({ url: "file:../mastra.db" }),
}),
});
Step 5: Update index.ts to register the agent
Replace the contents of src/mastra/index.ts with:
import { Mastra } from "@mastra/core/mastra";
import { PinoLogger } from "@mastra/loggers";
import { LibSQLStore } from "@mastra/libsql";
import { connectAIAgent } from "./agents/connect-ai-agent.js";
export const mastra = new Mastra({
agents: { connectAIAgent },
storage: new LibSQLStore({ url: "file:../mastra.db" }),
logger: new PinoLogger({ name: "Mastra", level: "info" }),
observability: { default: { enabled: true } },
});
Step 6: Run and verify the connection
Start your Mastra server:
npm run dev

Step 7: Run a live query in Mastra Studio
In Mastra Studio, open the chat interface and enter one of the following sample prompts:
List available catalogs from my connected data sources.

Build real-time, data-aware agents with Mastra and CData
Mastra and CData Connect AI together enable powerful AI-driven workflows where agents have live access to enterprise data and act intelligently without sync pipelines or manual integration logic.
Start your free trial today to see how CData can empower Mastra with live, secure access to 300+ external systems.






