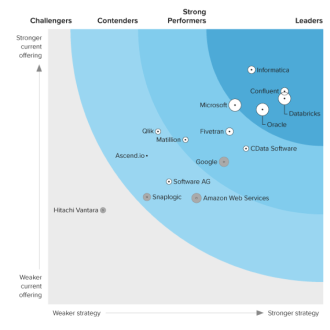
Discover how a bimodal integration strategy can address the major data management challenges facing your organization today.
Get the Report →Automated Continuous Amazon Athena Replication to Apache Cassandra
Use CData Sync for automated, continuous, customizable Amazon Athena replication to Apache Cassandra.
Always-on applications rely on automatic failover capabilities and real-time data access. CData Sync integrates live Amazon Athena data into your Apache Cassandra instance, allowing you to consolidate all of your data into a single location for archiving, reporting, analytics, machine learning, artificial intelligence and more.
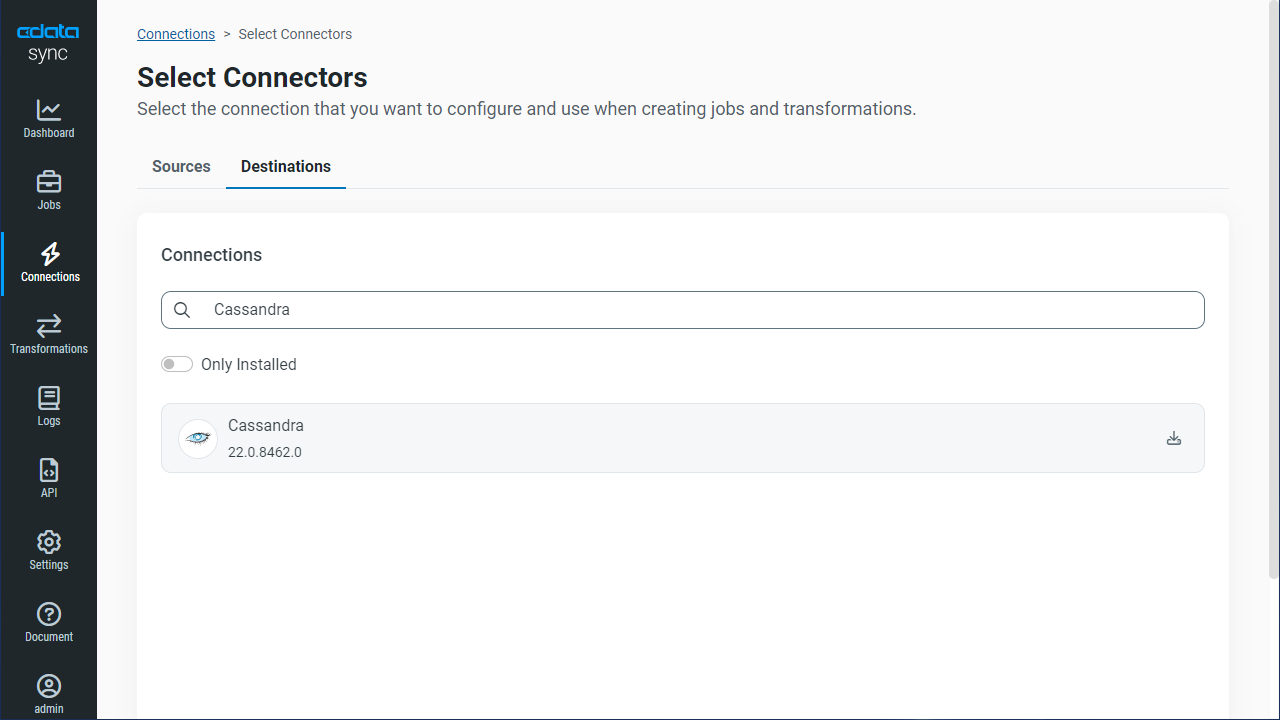
Configure Cassandra as a Replication Destination
Using CData Sync, you can replicate Amazon Athena data to Apache Cassandra. To add a replication destination, navigate to the Connections tab.
- Click Add Connection.
- Select Apache Cassandra as a destination.
![Configure a Destination connection to Apache Cassandra.]()
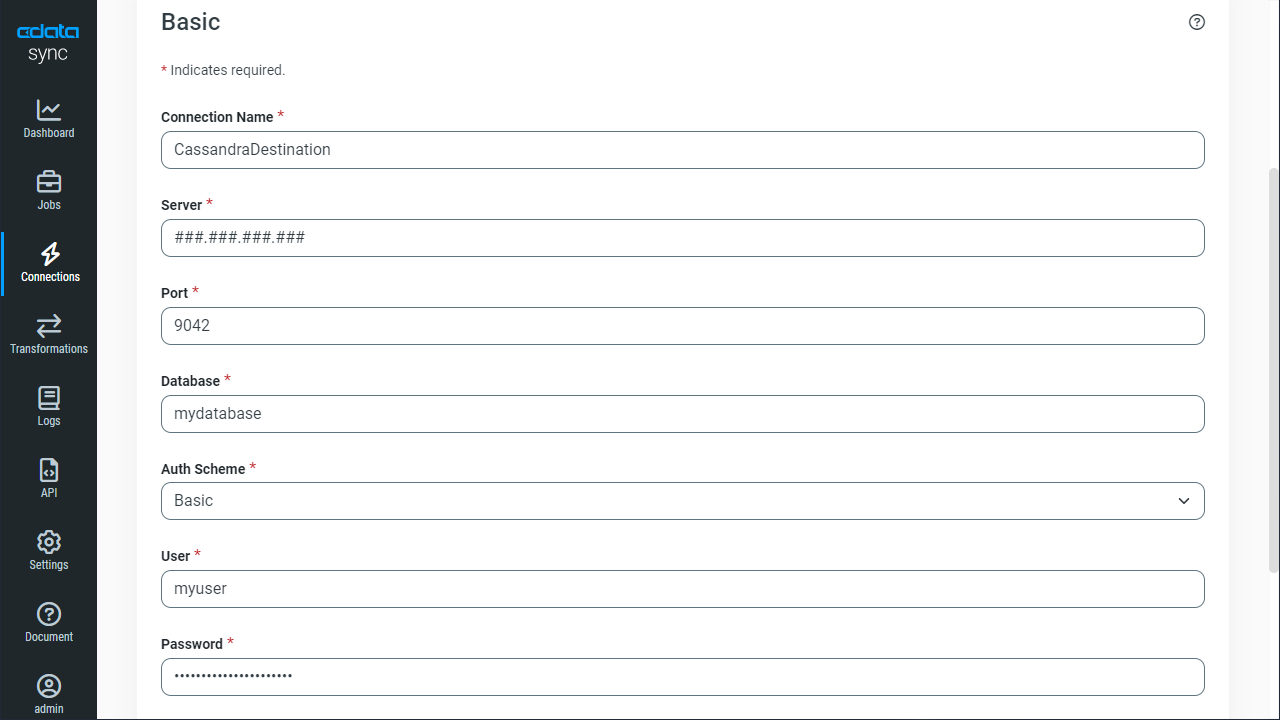
Enter the necessary connection properties. CData Sync supports Basic authentication with login credentials and the additional authentication features of DataStax Enterprise (DSE) Cassandra. The following sections detail connection properties your authentication method may require.
You need to set AuthScheme to the value corresponding to the authenticator configured for your system. You specify the authenticator in the authenticator property in the cassandra.yaml file. This file is typically found in /etc/dse/cassandra or through the DSE Unified Authenticator on DSE Cassandra.
Basic Authentication
Basic authentication is supported through Cassandra's built-in default PasswordAuthenticator.
- Set the AuthScheme property to 'BASIC' and set the User and Password properties.
- In the cassandra.yaml file, set the authenticator property to 'PasswordAuthenticator.'
Kerberos Authentication
Kerberos authentication is supported through DataStax Enterprise Unified Authentication.
- Set the AuthScheme property to 'KERBEROS' and set the User and Password properties.
- Set the KerberosKDC, KerberosRealm, and KerberosSPN properties.
- In the cassandra.yaml file, set the authenticator property to "com.datastax.bdp.cassandra.auth.DseAuthenticator."
- Modify the authentication_options section in the dse.yaml file, specifying the default_schema and other_schemas properties as 'kerberos.'
- Modify the kerberos_options section in the dse.yaml file, specifying the keytab, service_principle, http_principle and qop properties.
LDAP Authentication
LDAP authentication is supported through DataStax Enterprise Unified Authentication.
- Set the AuthScheme property to 'LDAP' and set the User and Password properties.
- In the cassandra.yaml file, set the authenticator property to "com.datastax.bdp.cassandra.auth.DseAuthenticator."
- Modify the authentication_options section in the dse.yaml file, specifying the default_schema and other_schemas properties as 'ldap.'
- Modify the ldap_options section in the dse.yaml file, specifying the server_host, server_port, search_dn, search_password, user_search_base, and user_search_filter properties.
Using PKI
You can specify a client certificate to authenticate CData Sync with SSLClientCert, SSLClientCertType, SSLClientCertSubject, and SSLClientCertPassword.
- Click Test Connection to ensure that the connection is configured properly.
![Configure a Destination connection.]()
- Click Save Changes.
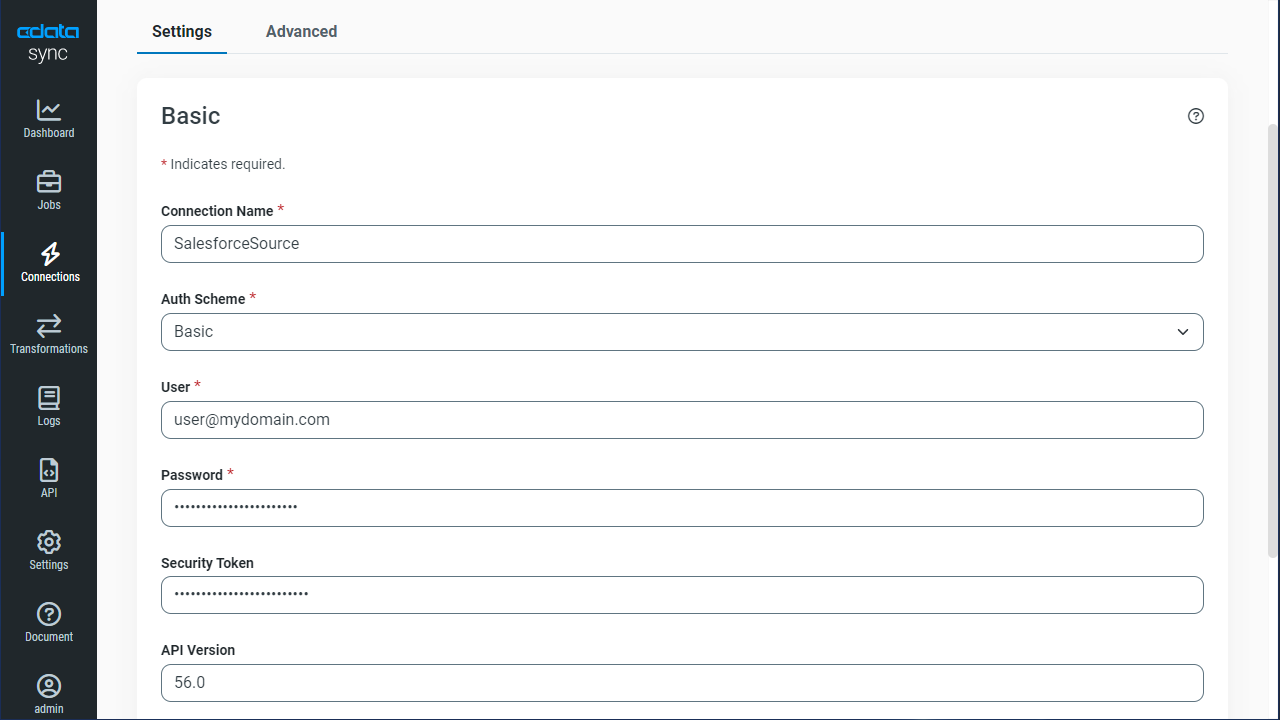
Configure the Amazon Athena Connection
You can configure a connection to Amazon Athena from the Connections tab. To add a connection to your Amazon Athena account, navigate to the Connections tab.
- Click Add Connection.
- Select a source (Amazon Athena).
- Configure the connection properties.
Authenticating to Amazon Athena
To authorize Amazon Athena requests, provide the credentials for an administrator account or for an IAM user with custom permissions: Set AccessKey to the access key Id. Set SecretKey to the secret access key.
Note: Though you can connect as the AWS account administrator, it is recommended to use IAM user credentials to access AWS services.
Obtaining the Access Key
To obtain the credentials for an IAM user, follow the steps below:
- Sign into the IAM console.
- In the navigation pane, select Users.
- To create or manage the access keys for a user, select the user and then select the Security Credentials tab.
To obtain the credentials for your AWS root account, follow the steps below:
- Sign into the AWS Management console with the credentials for your root account.
- Select your account name or number and select My Security Credentials in the menu that is displayed.
- Click Continue to Security Credentials and expand the Access Keys section to manage or create root account access keys.
Authenticating from an EC2 Instance
If you are using the CData Data Provider for Amazon Athena 2018 from an EC2 Instance and have an IAM Role assigned to the instance, you can use the IAM Role to authenticate. To do so, set UseEC2Roles to true and leave AccessKey and SecretKey empty. The CData Data Provider for Amazon Athena 2018 will automatically obtain your IAM Role credentials and authenticate with them.
Authenticating as an AWS Role
In many situations it may be preferable to use an IAM role for authentication instead of the direct security credentials of an AWS root user. An AWS role may be used instead by specifying the RoleARN. This will cause the CData Data Provider for Amazon Athena 2018 to attempt to retrieve credentials for the specified role. If you are connecting to AWS (instead of already being connected such as on an EC2 instance), you must additionally specify the AccessKey and SecretKey of an IAM user to assume the role for. Roles may not be used when specifying the AccessKey and SecretKey of an AWS root user.
Authenticating with MFA
For users and roles that require Multi-factor Authentication, specify the MFASerialNumber and MFAToken connection properties. This will cause the CData Data Provider for Amazon Athena 2018 to submit the MFA credentials in a request to retrieve temporary authentication credentials. Note that the duration of the temporary credentials may be controlled via the TemporaryTokenDuration (default 3600 seconds).
Connecting to Amazon Athena
In addition to the AccessKey and SecretKey properties, specify Database, S3StagingDirectory and Region. Set Region to the region where your Amazon Athena data is hosted. Set S3StagingDirectory to a folder in S3 where you would like to store the results of queries.
If Database is not set in the connection, the data provider connects to the default database set in Amazon Athena.
![Configure a Source connection (Salesforce is shown).]()
- Click Connect to ensure that the connection is configured properly.
- Click Save Changes.
Configure Replication Queries
CData Sync enables you to control replication with a point-and-click interface and with SQL queries. For each replication you wish to configure, navigate to the Jobs tab and click Add Job. Select the Source and Destination for your replication.
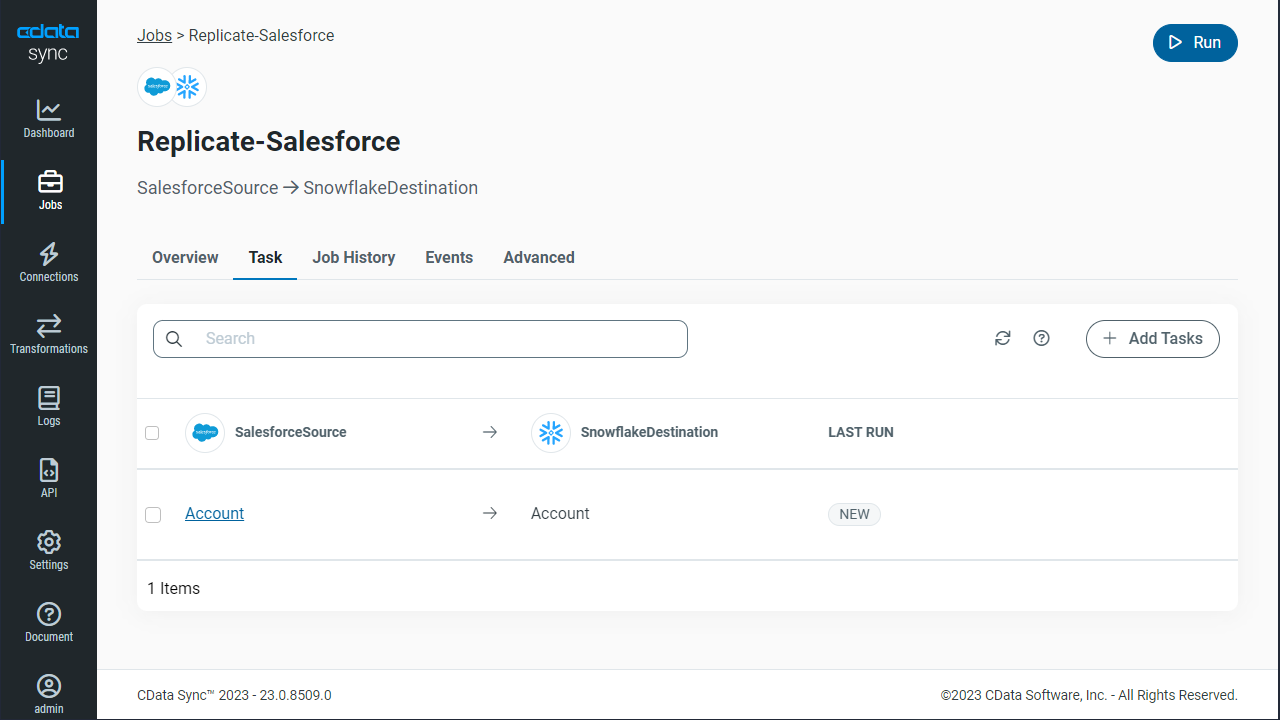
Replicate Entire Tables
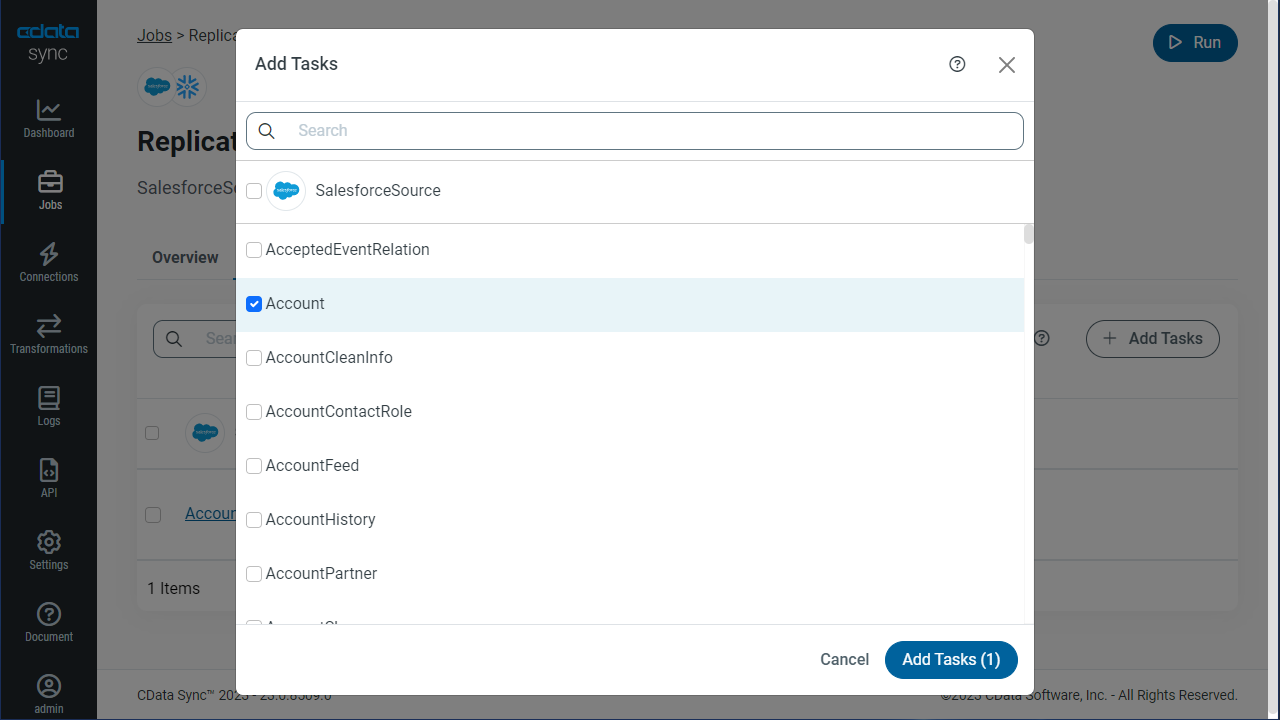
To replicate an entire table, click Add Tables in the Tables section, choose the table(s) you wish to replicate, and click Add Selected Tables.
Customize Your Replication
You can use the Columns and Query tabs of a task to customize your replication. The Columns tab allows you to specify which columns to replicate, rename the columns at the destination, and even perform operations on the source data before replicating. The Query tab allows you to add filters, grouping, and sorting to the replication.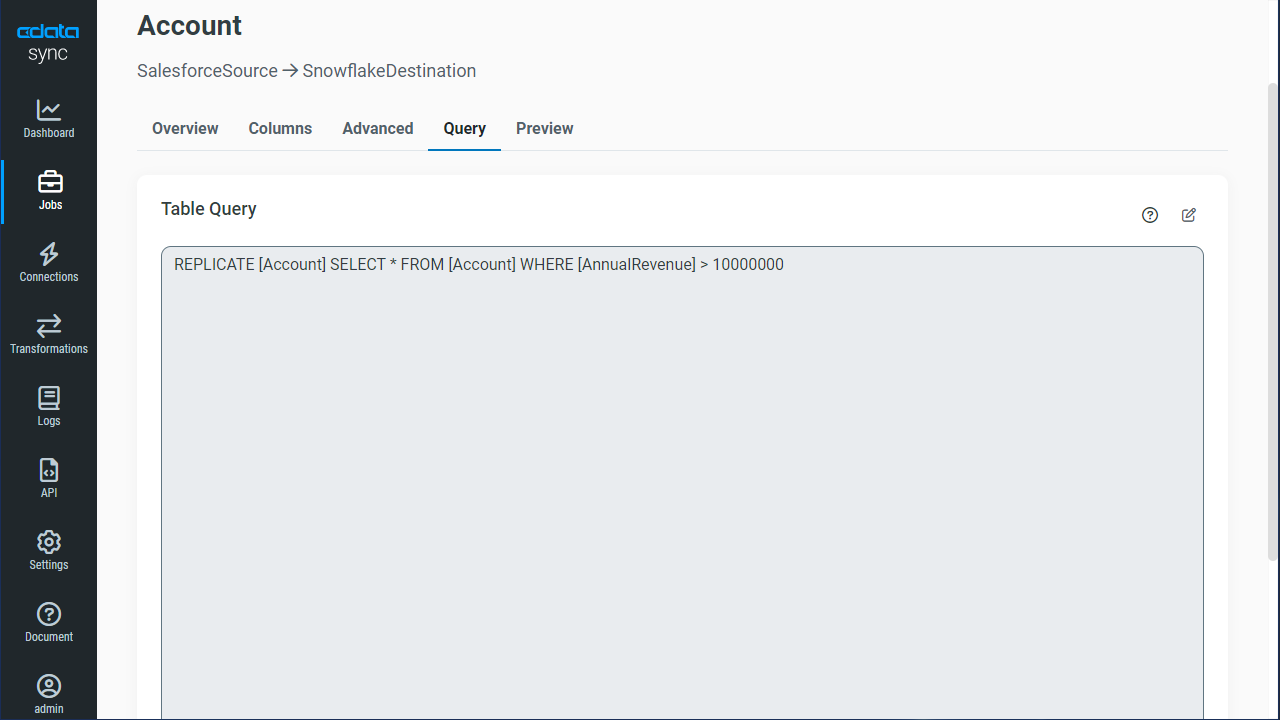
Schedule Your Replication
In the Schedule section, you can schedule a job to run automatically, configuring the job to run after specified intervals ranging from once every 10 minutes to once every month.
Once you have configured the replication job, click Save Changes. You can configure any number of jobs to manage the replication of your Amazon Athena data to Apache Cassandra.